aris2chat
Gold Member
- Feb 17, 2012
- 18,678
- 4,687
- 280
I'm not sure what you mean by something definitive.So in other words: The Russians have been hacking US government communications for years; as have the North Koreans, the Iranians, the Israelis, ect. I wonder when we get to see something definitive regarding the election?It is posted jointly by the Dept of Homeland Security's National Cybersecurity and Communications Integration Center (NCCIC) and the FBI. Since it's a joint report it may be available from other participating agencies. If that's not good enough for you, I suspect nothing would be.I wonder when we can have some indication that an actual secret report even exists? Maybe we could get at least one of the seventeen intelligence agencies to provide the public with a secret summery of the secret report. Some kind of verification of at least that much would be nice. Or are we just supposed to take their word for it?If Trump tries to cover up his involvement with Putin or bury information about the hacking, he will end up going the same way Nixon did. Republicans in congress would be perfectly happy with Pence as president, he would be far easier to deal with than Trump and lot less likely to do something really stupid that would hurt the party in the midterms.
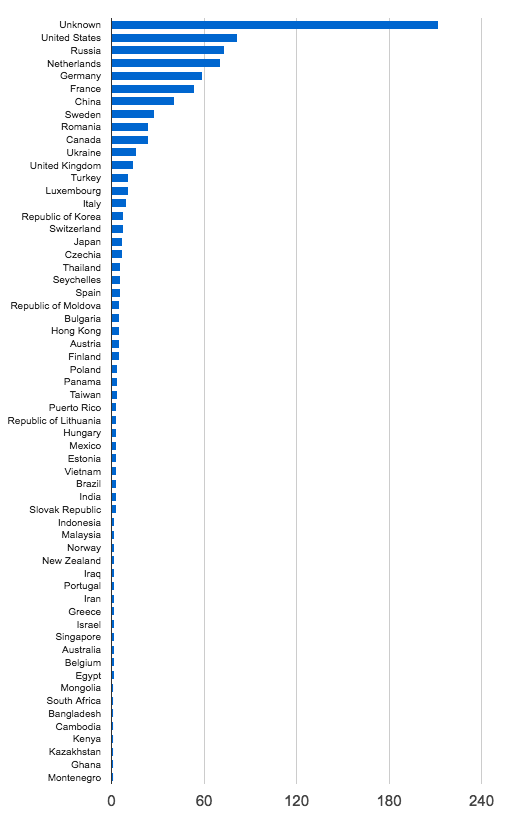
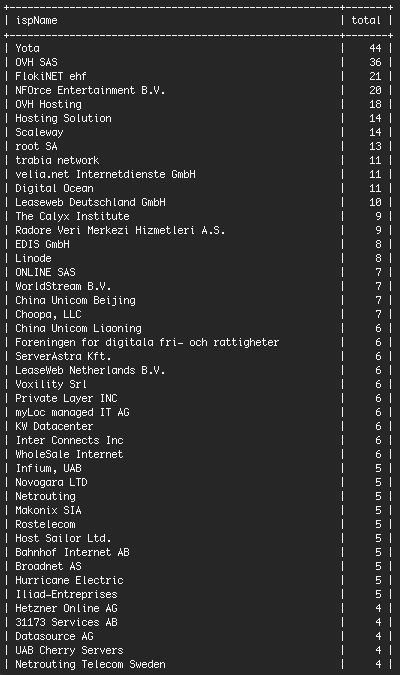
The joint report is a summary. Although it does contain an example of code and names common to both the current hacking and previous know Russian hacking, it does not contain details of the underlying analysis. Such details are not and should not be made available to the public.
https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296A_GRIZZLY STEPPE-2016-1229.pdf
We may see some additional information before Obama leaves office but I doubt it. Probably the next major release will come from Trump after the inauguration. He may reverse course in regard to Putin after he sees the details of the hack or he may bury it. If he buries it, there will probably be a Senate investigation committee. It's already being discussed.
I believe Obama stated they were going to release more information prior to Trump Inauguration. I think they're going to try & take him down before he's sworn in.
The Russians have been very busy this year.
1. Hacking the Pentagon to get into the Joint Chiefs of Staffs emails.
Russian hack almost brought the U.S. military to its knees
2. Hacking into the DNC databases, putting tons of FAKE news on social media outlets to elect Comrade Trump.
AND NOW THE LATEST--our electric power grids--they have found the same Russian malware.
Apparently the FBI has sent out a message to all power grids in this country to look for this Russian malware they've been using and one (so far) has been found in Vermont. They refer to this malware as the GRISSLEY STEEP MALWARE. This is the same malware that was used to hack DNC databases.
"The indicators from the malicious software found on a Burlington Electric Company laptop match those on malware found in the Democratic National Committee computers that the US government has blamed on Russians, the Department of Homeland Security said Saturday.
DHS spokesman Todd Breasseale said the department's investigation into the cyber intrusion on the computer is ongoing and he couldn't comment further.
The DHS's acknowledgment is the first such confirmation by the government that the malware is the same as the code used in malicious cyber activity that the US government has blamed on Russian hackers attempting to influence November's election.
It comes a day after Burlington Electric announced it found the malicious software on a computer that was not connected to its grid control systems. Both the Department of Homeland Security and the utility said Saturday there are no indications that the electric grid was breached.
The DHS and the FBI made a 13-page report public Thursday with information about the malware code -- which was found on Democratic National Committee computers -- and urged all entities to check for it.
Alleged Russian malware found on Vermont utility's laptop - CNN.com
What does Comrade Trump say about all this--as of tonight December 31, 2016. "President-elect Donald Trump reiterated his doubts Saturday that Russia was behind cyber-meddling in the US election, saying such a crime would be difficult to prove."
Trump casts hacking doubts again - CNNPolitics.com

Maybe not so hard to prove
http://www.nytimes.com/2016/11/11/world/europe/trump-campaign-russia.html?_r=1
not
media got hooked again

 Holy cow.. If you knew how good these folks were at accessing the HARD targets, Hillary's server, the DNC and Podesta's phone would be child's play.. Any of THOUSANDS of hackers who happened to use Russian malware and tools (not Russian Intel Agency tools) could have done this on a lark. These devices were WIDE open. Commercial spyhunter s/w protection doesn't even bother them with the type of phishing attacks that Podesta's phone was. In fact, the spear-fishing attack that opened up his phone was discussed publicly. He inquired to IT as to a memo that SEEMED to come from them. But in the reply, (the story goes), The IT person said that his "spell-checker" changed a word that told Podesta (or assistant) that it was OK to open the malicious file.
Holy cow.. If you knew how good these folks were at accessing the HARD targets, Hillary's server, the DNC and Podesta's phone would be child's play.. Any of THOUSANDS of hackers who happened to use Russian malware and tools (not Russian Intel Agency tools) could have done this on a lark. These devices were WIDE open. Commercial spyhunter s/w protection doesn't even bother them with the type of phishing attacks that Podesta's phone was. In fact, the spear-fishing attack that opened up his phone was discussed publicly. He inquired to IT as to a memo that SEEMED to come from them. But in the reply, (the story goes), The IT person said that his "spell-checker" changed a word that told Podesta (or assistant) that it was OK to open the malicious file. That's not a PayPal type deal..
That's not a PayPal type deal..